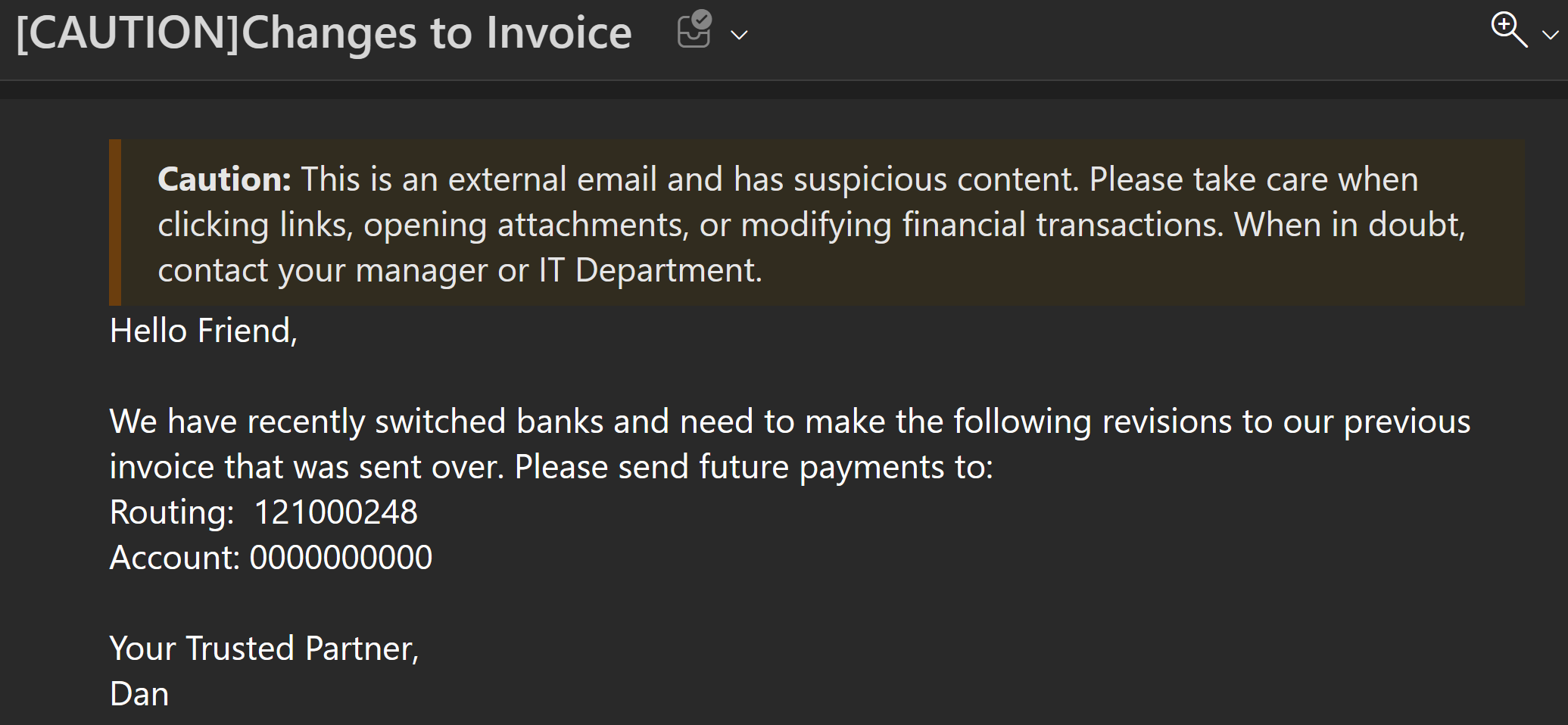
Microsoft Defender for Office has plenty of features for fraud detections involving homoglyph domains and BEC, but how do you protect against supply chain attacks where an attacker has compromised a valid account from one of your vendors? This post will attempt to help you create Fraud Detection alerts with Exchange Transport Rules and Custom Sensitive Info Types to help identify attacks from your trusted vendors that have experienced a Business Email Compromise (BEC) breach. I will continuously update this guide as I receive feedback for improvements and perform additional research on broader threat intelligence datasets.
Note: I generated this keyword list by asking GPT-4 for sample BEC messages, updating the keyword list and asking GPT-4 to write new sample messages excluding the keyword list, and repeated until it couldn’t write anything coherent. I have not tested this Custom Sensitive Info Type for potential Fraud Detection on real-world data, so I cannot provide any estimates for false-positives at this time…but I’m looking for volunteers!
What is Business Email Compromise?
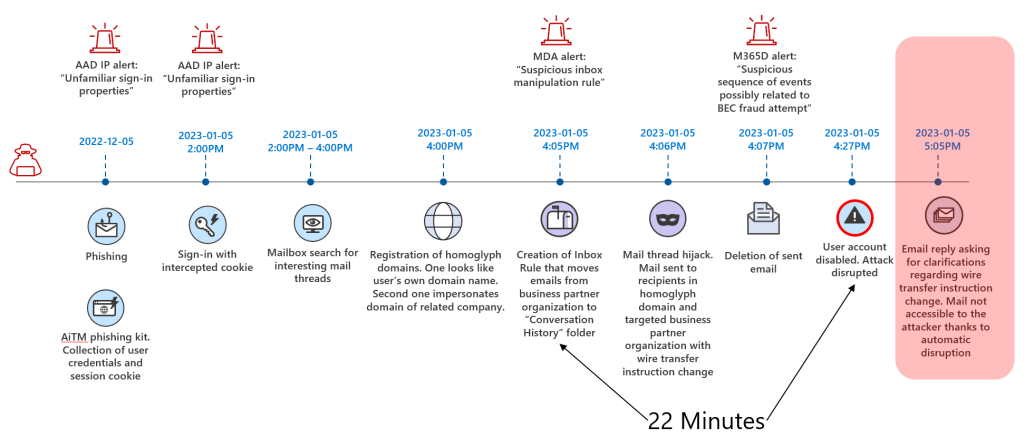
Business Email Compromise (BEC) is a form of email cybercrime where an attacker scams a business to defraud the company. BEC attacks have exposed organizations worldwide to billions of dollars in losses. A BEC scam typically involves a cybercriminal hacking and spoofing emails to impersonate a company’s supervisors, CEO, or vendors. This may include a compromised user account or registering a homoglyph domain. The scammer then requests a seemingly legitimate business payment, such as an invoice or a gift card, or asks for sensitive data that they can use in another scam. BEC scams are hard to detect and can cause serious financial and reputational damage to businesses. Therefore, it is important to take the threat seriously and implement security measures to prevent and mitigate BEC attacks.
The illustration above shows the Automatic Attack Disruption for a BEC kill chain when you’re using Microsoft Defender XDR. The anomalous login attempt is detected by Microsoft Entra’s Azure AD P2 after a successful Adversary in the Middle (AiTM) attack steals the session cookies. Once the attacker creates forwarding rules in the compromised mailbox, it is detected by Microsoft Defender for Cloud Apps via the Suspicious Inbox Manipulation Rule detection. Less then 22 minutes later, Microsoft Defender XDR correlates alerts from the multi-stage attack into a single incident and locks out the user account. When you’re using Microsoft Defender for Identity, the user account is locked out both in Azure AD and on-prem AD DS. If you’re using a third-party IAM service, like Okta or Ping, and you have AD DS set as the source of truth, then the account will be locked out in your IAM provider on the next sync as well.
How do I create a Custom Sensitive Info Type in Microsoft Purview?
Microsoft Data Loss Protection service comes with 300+ identifiers for different types of Personally Identifiable Information (PII) around the globe. We will leverage the US Bank account detections along with international banking detections with custom keyword lists that I have aggregated from sample attack messages.
First, login to https://compliance.microsoft.com and select Data Classification > Classifiers > Sensitive Info Types and then click Create Sensitive Info Type.
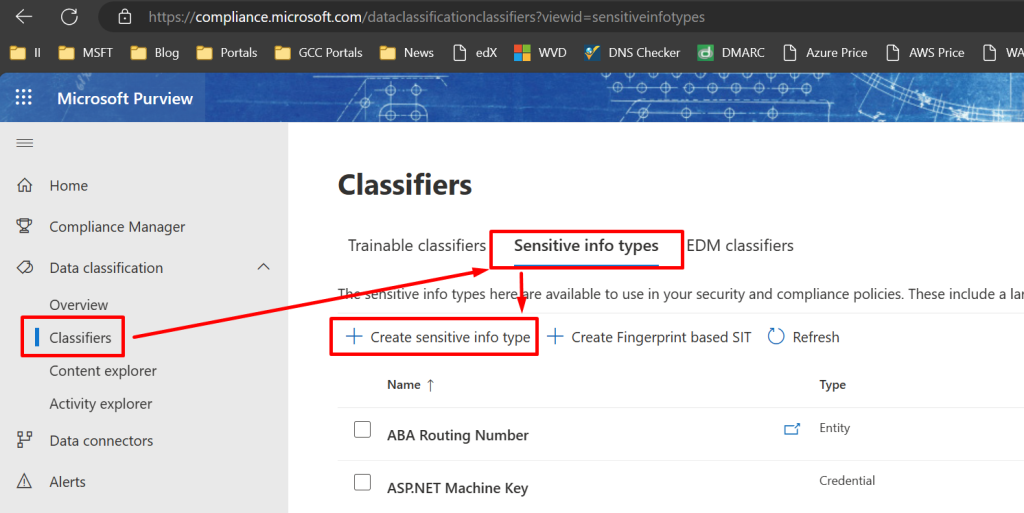
In the Name Your Sensitive Info Type page, use the following:
- Name: Fraud Detection
- Description: Detects potential fraud from vendors/suppliers that have suffered a Business Email Compromise(BEC) attack.
- Click Next.
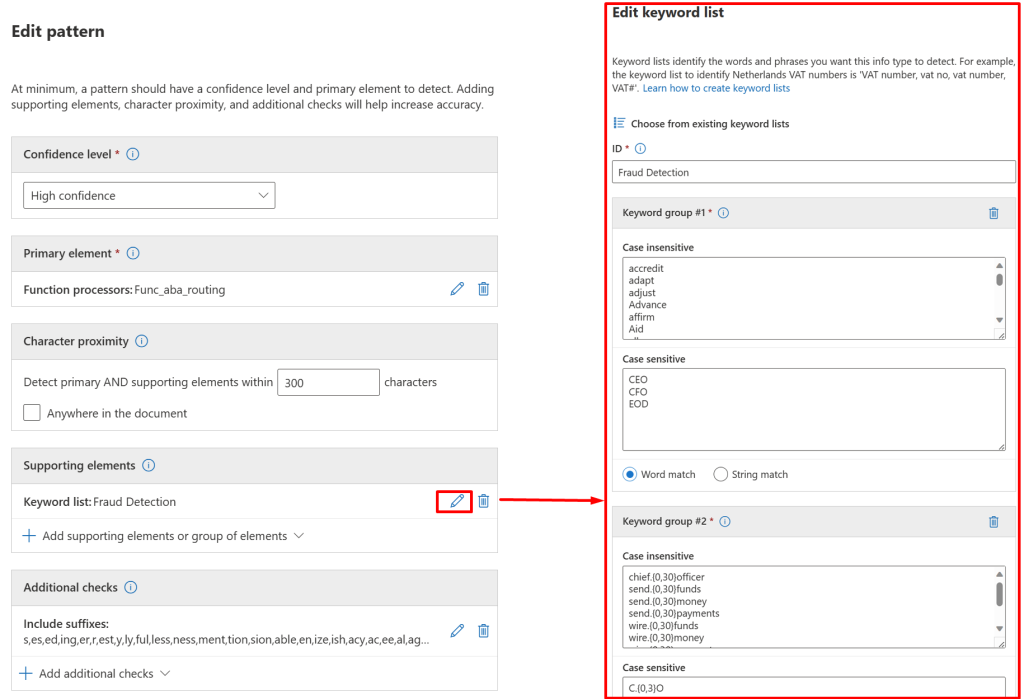
The Define Patterns for This Sensitive Info Type section will take a few minutes to setup. Start by creating a new pattern and in the Primary Element area, select Functions > Choose Functions > Func_aba_routing.
Under the Supporting Elements area, we’re going to create a Keyword List and populate it with the following.
Keyword Group #1 – Case Insensitive – set this group to Word Match.
# bic
aba
aba number
aba#
abarouting#
abaroutingnumber
account
accredit
ach
adapt
adjust
advance
affirm
aid
allowance
alter
alternate
amend
americanbankassociationrouting#
americanbankassociationroutingnumber
ammend
annul
approve
assist
assistance
authorization
authorize
balance
bank
bank account #
bank account no.
bank account number
bank acct #
bank acct no.
bank acct number
bank identifier code
bankrouting#
bankroutingnumber
begin
benefit
bic #
bic code
bic number
bic#
bonus
boost
brokerage
cancel
carefully
change
checking
checking account
checking account #
checking account no.
checking account number
checking acct #
checking acct no.
checking acct number
code identificateur de banque
code swift
commission
compensation
confidential
configure
confirm
contact
convert
cooperation
correct
credit
crisis
critical
crucial
customer
deal
debit account
debit account #
debit account no.
debit account number
debit acct #
debit acct no.
debit acct number
delay
deliver
deposit
different
direct deposit
discerning
discount
discreet
distress
dividend
eliminate
emergency
enable
equity
essential
establish
excess
exclusive
expedite
facilitate
fast
fee
follow
forward
fraudulent
funds
future
gift
gift card
give
halt
handout
hasten
help
hurry
immediately
imperative
important
insist
instruct
instruction
interim
intimate
invoice
iso 9362
iso9362
issue
lawyer
le numéro bic
le numéro de swift
legal
modify
money
necessary
new
overnight
overturn
partner
pay
payment
payroll
permit
post
pressing
private
prize
quick
rapid
rapide #
refund
relay
remain
remainder
remaining
remit
remove
repeal
request
rescind
resend
residual
return
revise
revoke
reward
route
routing
routing #
routing no
routing number
routing transit number
routing#
royalty
rtn
rush
savings account #
savings account no.
savings account number
savings account.
savings acct #
savings acct no.
savings acct number
serious
service
settle
setup
ship
stipend
substitute
supplier
support
surplus
suspend
suspicious
swift code
swift number #
swift numéro d'acheminement
swift routing number
swift#
swiftcode
swiftnumber
swiftroutingnumber
switch
system
terminate
terms
test
time being
today
transaction
transfer
transmit
trust
update
urgent
vendor
verify
vest
vital
void
volatile
warrant
wire
Keyword Group #1 – Case Sensitive
CEO
CFO
EODKeyword Group #2 – Case Insensitive – set this group to String Match as these are all regular expressions (regex).
chief.{0,30}officer
send.{0,30}funds
send.{0,30}money
send.{0,30}payments
wire.{0,30}funds
wire.{0,30}money
wire.{0,30}payment
transfer.{0,30}funds
transfer.{0,30}money
transfer.{0,30}paymentsKeyword Group #2 – Case Sensitive
C.{0,3}OPress Done to finalize the word list and then proceed to…
Additional Checks – include the following suffixes.
s,es,ed,ing,er,r,est,y,ly,ful,less,ness,ment,tion,sion,able,en,ize,ish,acy,ac,ee,al,age,dom,ism,ity,ty,ship,xion,less,enYou’re ready to save the pattern. It should look something like this:
Next, we’re going to make two copies of this pattern and replace the Primary element with func_iban and func_credit_card.
Optional: you can create a fourth sensitive info type pattern using the Regular Expressions from Keyword Group #2 as the Primary Element. This would be to detect emails where the attacker is attempting a Vishing (voice phishing) attack and does not include any financial data in the email, but offers to provide it over the phone instead. Warning: this has the potential to increase the false positive rate, as there are no supporting financial numbers in this pattern.
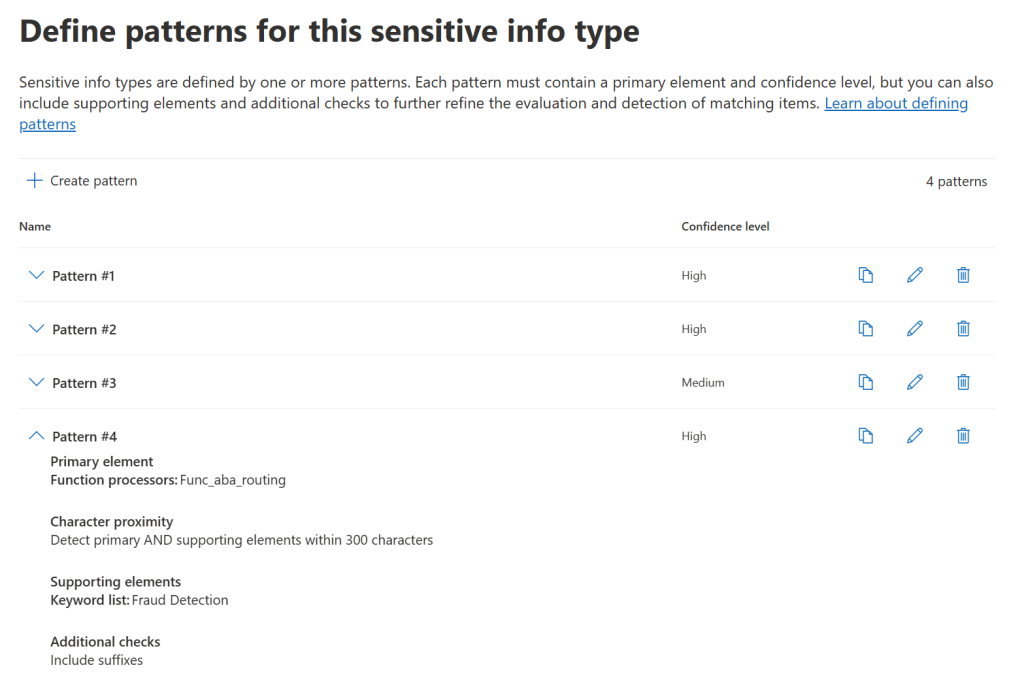
Once you have your three or four patterns created, save it, select High or Medium confidence levels, and let’s move on to Exchange Online.
Creating an Exchange Transport Rule to warn of potential Fraud
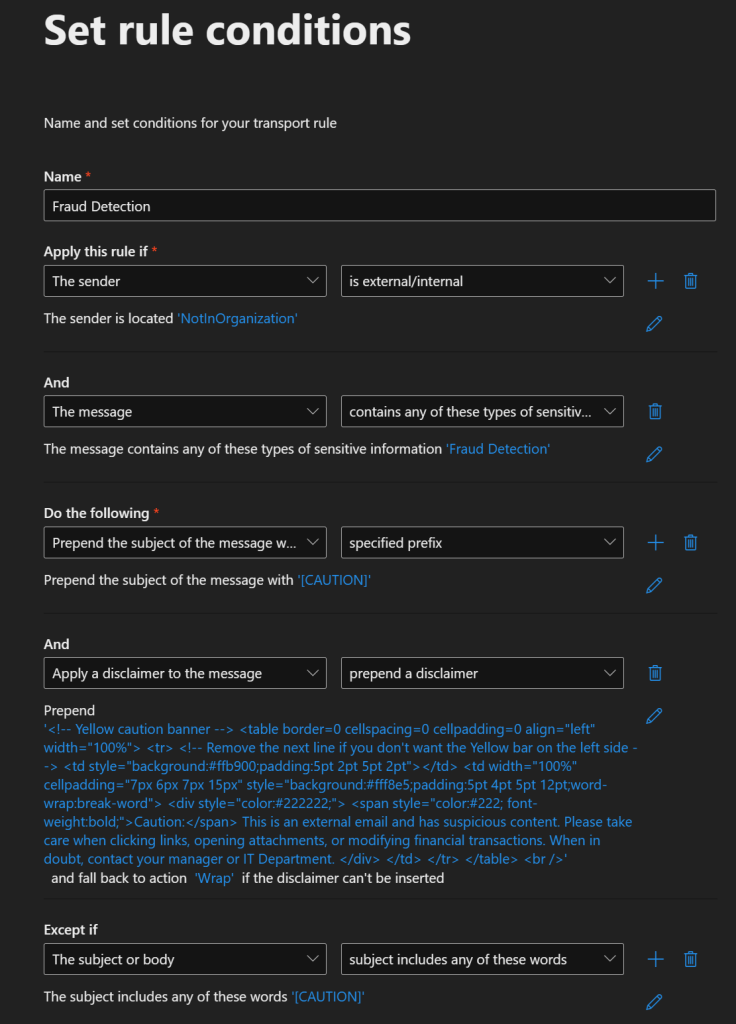
For this section, head over to Exchange admin center (microsoft.com) and select Add a rule > Create a New Rule. Select the following options:
- Name: Fraud Detection
- Apply this rule if The Sender is external/internal > NotInOrganization
- And: the message contains any of these types of sensitive information > Fraud Detection
- Do the following:
- Prepend the subject of the message with the specified prefix > [CAUTION]
- Apply a disclaimer to the message > prepend a disclaimer:
<!-- Yellow caution banner -->
<table border=0 cellspacing=0 cellpadding=0 align="left" width="100%">
<tr>
<!-- Remove the next line if you don't want the Yellow bar on the left side -->
<td style="background:#ffb900;padding:5pt 2pt 5pt 2pt"></td>
<td width="100%" cellpadding="7px 6px 7px 15px" style="background:#fff8e5;padding:5pt 4pt 5pt 12pt;word-wrap:break-word">
<div style="color:#222222;">
<span style="color:#222; font-weight:bold;">Caution:</span>
This is an external email and has suspicious content. Please take care when clicking links, opening attachments, or modifying financial transactions. When in doubt, contact your manager or IT Department.
</div>
</td>
</tr>
</table>
<br />- Except if > Subject or Body > Subject Includes these words: [CAUTION]
That last exception will prevent an email thread from being repeatedly labeled [CAUTION].
Closing Thoughts on Fraud Detection Alerts with Exchange Transport Rules and Custom Sensitive Info Types
While Defender for Office P2 is great at stopping BEC attacks from being sent from your organization, it needs a little help when one of your vendors is compromised. This caution label should be used as a counterpart to your security awareness training, and not as a replacement for it. (Microsoft Defender for Office P2 now contains security awareness training!)
You may also consider applying this Fraud Detection Alert to internal messages in the Exchange Transport Rule as well, as I have seen cases where an employee’s account is compromised and asks HR to modify their direct deposit payments. Either way, utilizing Custom Sensitive Info Type with Exchange Transport Rules just provides a warning message. At worst it will annoy your users, and at best it will prevent a BEC attack.
Leave a note in the comments about your thoughts on Fraud Detection Alerts with Exchange Transport Rules and Custom Sensitive Info Types, and if you have any suggestions for improvement!